Por Stephen Nellis e Max A. Cherney
http://dlvr.it/T28Ntm
quarta-feira, 31 de janeiro de 2024
ANPD adverte governo do Distrito Federal por dados vazados de estudantes
Falha de segurança no sistema I-Educar permitiu acesso a dados pessoais de 1 milhão de alunos da rede pública, em 2021.
http://dlvr.it/T27QZr
http://dlvr.it/T27QZr
Anatel mostra regras para novas concessões de telefonia
Proposta, um plano B se falharem negociações com as atuais concessionárias, tem orelhões gratuitos, nova tarifação, contratos e metas de universalização.
http://dlvr.it/T273Kn
http://dlvr.it/T273Kn
Telesc?pio James Webb capta imagens de 19 gal?xias com resolu??o in?dita
Imagens capturadas pelo telesc?pio espacial James Webb e divulgadas na segunda-feira, 29, mostram com detalhes in?ditos 19 gal?xias espirais relativamente pr?ximas da Via L?ctea, onde est? o planeta Terra.
http://dlvr.it/T26wXQ
http://dlvr.it/T26wXQ
Fique alerta e se proteja: estes s?o os golpes do Pix mais famosos
Lan?ado em 2020, o Pix rapidamente virou o principal meio de transfer?ncia de dinheiro entre contas. O Brasil fechou 2023 com 144,8 milh?es de pessoas com alguma chave cadastrada no Banco Central. A facilidade para transferir dinheiro, por outro lado, chamou aten??o de cibercriminosos, que viram uma oportunidade de aplicar os chamados golpes do Pix.
http://dlvr.it/T26HKT
http://dlvr.it/T26HKT
terça-feira, 30 de janeiro de 2024
Pol?cia alem? apreende US$2,17 bi em bitcoins na a??o "mais ampla" de todos os tempos
(Reuters) - A pol?cia alem? confiscou 50.000 bitcoins no valor de 2,17 bilh?es de d?lares na "mais ampla" apreens?o de criptomoedas j? realizada no pa?s, informou em um comunicado nesta ter?a-feira.
http://dlvr.it/T25qVk
http://dlvr.it/T25qVk
Hackers atacam Hospital do Câncer no Rio e consultas são canceladas
Segundo o hospital, anotações são feitas à mão e não estão sendo feitas novas marcações. Ataque aconteceu no domingo, dia 28/01, e todos os servidores de TI foram desligados.
http://dlvr.it/T24rCW
http://dlvr.it/T24rCW
IA generativa dá vantagem competitiva única ao Machado Meyer Advogados
Ferramenta, desenvolvida internamente, auxilia os profissionais do direito em diversas tarefas, maximizando o capital intelectual. "Identificar padrões e insights é algo estratégico”, pontua Paulo Silvestre de Oliveira Junior, head de inovação e desenvolvimento do escritório.
http://dlvr.it/T24Swp
http://dlvr.it/T24Swp
Neuralink, de Elon Musk, implanta chip em c?rebro humano
(Reuters) - O primeiro paciente humano recebeu um implante da startup de chips cerebrais Neuralink no domingo e est? se recuperando bem, disse o bilion?rio fundador da empresa, Elon Musk.
http://dlvr.it/T24LBj
http://dlvr.it/T24LBj
Popula??o da China encolhe e pressiona aposta em alta tecnologia; entenda
or d?cadas o pa?s mais populoso do mundo, a China vive agora ?s voltas com o encolhimento de sua popula??o que, ali?s, est? ficando mais velha. Em maio do ano passado, as Na??es Unidas declararam que...
http://dlvr.it/T23glg
http://dlvr.it/T23glg
segunda-feira, 29 de janeiro de 2024
Elon Musk anuncia 1? implante de chip cerebral da Neuralink em ser humano
O bilion?rio Elon Musk, CEO do X (ex-Twitter), anunciou hoje o primeiro implante do chip cerebral da Neuralink em um ser humano. O dispositivo de interface c?rebro-computador (BCI, na sigla em ingl?s) tem como objetivo permitir que pessoas com paralisia controlem equipamentos externos com seus pensamentos.
http://dlvr.it/T23F2n
http://dlvr.it/T23F2n
Fadiga com IA Generativa aponta 2024 morno para investimentos em TI
Projeções do Garter apontam para investimentos de US$ 5 bilhões (+6,8%), dominados por áreas tradicionais. Serviços de TI ganham impacto e passam a ser o maior segmento de gastos com TI.
http://dlvr.it/T22Gs4
http://dlvr.it/T22Gs4
Bastille Networks Raises $44 Million to Secure Wireless Devices
Goldman Sachs leads wireless threat intelligence firm Bastille Networks’ $44 million Series C funding round.
The post Bastille Networks Raises $44 Million to Secure Wireless Devices appeared first on SecurityWeek.
http://dlvr.it/T21g6f
The post Bastille Networks Raises $44 Million to Secure Wireless Devices appeared first on SecurityWeek.
http://dlvr.it/T21g6f
Jap?o afirma que seu m?dulo lunar 'retomou opera??es'
O m?dulo lunar japon?s SLIM retomou as opera??es, o que sugere que conseguiu restaurar o fornecimento de energia, anunciou a ag?ncia espacial JAXA nesta segunda-feira (29).
http://dlvr.it/T21Mq8
http://dlvr.it/T21Mq8
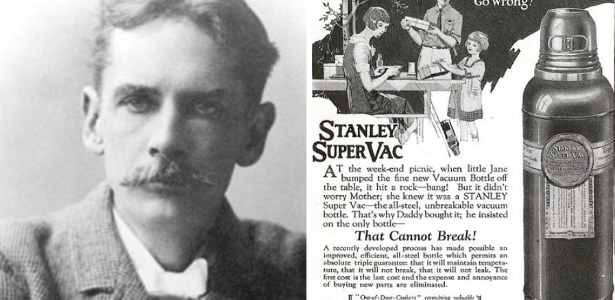
Inven??o por acidente: Stanley, do copo, fez mais do que voc? imagina
A marca Stanley explodiu com a venda de seus famosos copos t?rmicos, que prometem manter as bebidas quentes ou geladas por longas horas. Poucos sabem, por?m, que a hist?ria do objeto come?ou em 1913, quando William Stanley Jr., f?sico e engenheiro, criou a primeira garrafa t?rmica de isolamento a v?cuo feita totalmente em a?o.
http://dlvr.it/T217LQ
http://dlvr.it/T217LQ
domingo, 28 de janeiro de 2024
Jap?o diz que sua sonda lunar 'retomou opera??es'
A sonda lunar japonesa SLIM retomou suas opera??es, o que sugere que conseguiu restaurar o fornecimento de energia, anunciou a ag?ncia espacial JAXA nesta segunda-feira (29, noite de domingo no Brasil).
http://dlvr.it/T20lgR
http://dlvr.it/T20lgR
Rover Perseverance encontra sedimentos de antigo lago em Marte; entenda a descoberta
descoberta de sedimentos de um antigo lago na base da cratera Jezero pelo Rover Perseverance refor?a a esperan?a de que vest?gios de vida possam ser encontrados em amostras de solo e rochas coletada...
http://dlvr.it/T202v7
http://dlvr.it/T202v7
sábado, 27 de janeiro de 2024
Sensor de papel?o e ouro poder? monitorar a qualidade da ?gua por R$ 0,50
Um sensor descart?vel de baixo custo e uso simples, feito de papel?o e contendo nanopart?culas de ouro, poder? vir a ser uma ferramenta ?til para monitorar a qualidade da ?gua consumida pela popula??o.
http://dlvr.it/T1xfwn
http://dlvr.it/T1xfwn
sexta-feira, 26 de janeiro de 2024
Microsoft Teams fica fora do ar para milhares de usu?rios, diz Downdetector
(Reuters) - Os servi?os do aplicativo Microsoft Teams ficaram fora do ar para milhares de usu?rios nesta sexta-feira, de acordo com o site de rastreamento de interrup??es Downdetector.com.
http://dlvr.it/T1wYNs
http://dlvr.it/T1wYNs
Estrela que emite fuma?a ? descoberta na Via L?ctea
Um novo tipo de estrela, que permanece silenciosa durante longos per?odos de tempo antes de exalar uma nuvem de fuma?a, acaba de ser detectada pelos cientistas.
http://dlvr.it/T1wLWw
http://dlvr.it/T1wLWw
5G: Disponibilidade real varia de 11,1% a 7,1% no Brasil
Dados foram apurados pela OpenSignal na Claro, TIM e Vivo. Em streaming, a TIM fica à frente das rivais. Mas a Claro tem maior velocidade de download.
http://dlvr.it/T1vxmx
http://dlvr.it/T1vxmx
Oi contrata Fabricio Bindi, ex-TIM, para fibra. Rogério Takanayagi vai para Estratégia e Transformação
A saída de Rodrigo Abreu do cargo de CEO já promove as primeiras mudanças na Oi. Fábricio Bindi, ex-TIM, assume a diretoria de Varejo Empresarial para cuidar da estratégia de fibra óptica. Rogerio Takayanagi retorna à diretoria de Estratégia e Trasnformação, praa cuidar da Cliente Co.
http://dlvr.it/T1vKxb
http://dlvr.it/T1vKxb
quinta-feira, 25 de janeiro de 2024
Tesla Hack Earns Researchers $100,000 at Pwn2Own Automotive
Over $1 million paid out in the first two days of Pwn2Own Automotive for Tesla, infotainment and EV charger hacks.
The post Tesla Hack Earns Researchers $100,000 at Pwn2Own Automotive appeared first on SecurityWeek.
http://dlvr.it/T1srTw
The post Tesla Hack Earns Researchers $100,000 at Pwn2Own Automotive appeared first on SecurityWeek.
http://dlvr.it/T1srTw
Thousands of GitLab Instances Unpatched Against Critical Password Reset Bug
Over 5,000 GitLab servers have yet to be patched against CVE-2023-7028, a critical password reset vulnerability.
The post Thousands of GitLab Instances Unpatched Against Critical Password Reset Bug appeared first on SecurityWeek.
http://dlvr.it/T1srCH
The post Thousands of GitLab Instances Unpatched Against Critical Password Reset Bug appeared first on SecurityWeek.
http://dlvr.it/T1srCH
Data analytics on online services under GDPR: Legal basis for processing
Under the EU General Data Protection Regulation, organizations must have lawful grounds to process personal data, within limited legal bases outlined in Article 6.
It is common to come across privacy notices indicating personal data is being processed for analytics purposes. In such cases, a single legal basis is often pointed out. But can data analytics be considered only one purpose for processing, grounded in a single legal basis under the GDPR?
Analytics: What are we talking about?
Analytical data is used to support systematic analysis, such as inspecting, transforming and modeling data to extract useful information, draw conclusions and patterns, and support decision-making.
Data analytics can be divided into two layers: the raw data layer, comprising user events and actions, and the metadata layer, processed and analyzed information derived from the raw data that is transformed into meaningful insights through techniques or tools.
The raw data layer represents the granular and detailed information collected during user interactions with applications and systems, while the analytics metadata layer represents the higher level insights and conclusions drawn from analyzing such raw data.
User actions refer to the various activities and behaviors individuals perform while interacting with an application, like user authentication, button clicking, typing, data inputting, scrolling, downloading, uploading, sharing and liking.
User events are specific occurrences that are tracked or logged during a user's interaction with a system or application and do not necessarily require affirmative actions. Events can be page or frame views, system errors, or transactional events.
As for the metadata layer, common events, in e-commerce apps for example, include the shopping cart abandonment rate, conversion rate and average order value — that is, the average amount spent by customers in a single transaction.
It is worth mentioning that some websites collect analytics through cookies, which then trigger application of the EU's ePrivacy Directive.
Purposes of processing for data analytics
Determining the processing purpose for data analytics should delve into the intent of the data collection and its intended use. This is because the same user data can be used for multiple analyses and, therefore, collected for different purposes. As so, not all purposes of data processing can be based on the same legal basis and may require different privacy by-design implementations to ensure lawfulness, such as:
* Monitoring application security and availability — like analyzing app crashes, debugging and troubleshooting, detecting anomalies, ensuring security traceability, and assuring app performance.
* Improving service, including by uncovering user patterns, trends, correlations and insights to improve existing and future features, as well as evaluating user engagement and creating user personas.
* Utilizing indirect funding models, where data is shared with third parties.
* Integrating business intelligence needs, such as supporting strategic decision-making and defining and monitoring key performance indicators.
* Utilizing service personalization, where the app itself contains an analytics board, or when specific user events and actions trigger specific app events, such as knowledge article recommendations.
This list is not exhaustive. Data analysts will likely find other interesting potential uses.
Anonymized processing of data analytics
Some organizations may have an option to process anonymized data for analytical purposes. Anonymized data is not identified or identifiable, and thus, it is not personal data and is out of the scope of privacy protection, as stated in GDPR Recital 26. The problems of defining a legal basis would not apply.
Application security, availability and service personalization
Monitoring application security, availability and service personalization may be considered parts of the service provision and, thus, able to rely on the performance of a contract — Article 6(1)(b) of the GDPR — as the legal basis for processing. It is generally in the user's interest to have means to keep data secure and protected when contracting a service, and logging is a common feature of most security frameworks. When the service value is intrinsically connected to in-app analytics or content personalization, such processing also counts as part of the service.
In such cases, consent is not an available legal basis because users generally could not freely withdraw consent while continuing to use the service. The European Data Protection Board's guidelines on consent state, "Generally, consent can only be an appropriate lawful basis if a data subject is offered control and is offered a genuine choice with regard to accepting or declining the terms offered or declining them without detriment."
Conversely, when the in-app analytics or personalized features are optional or not essential for the service provision, consent or legitimate interest may serve as a legal basis.
Service improvement
EDPB guidelines emphasize that Article 6(1)(b) would generally not be an appropriate lawful basis for processing personal data to improve service. In the EDPB's words, "while the possibility of improvements and modifications to a service may routinely be included in contractual terms, such processing usually cannot be regarded as being objectively necessary for the performance of the contract with the user."
This is also in the EDPB's binding decision on the dispute submitted by Ireland's Data Protection Commission regarding WhatsApp Ireland, in which the EDPB decided the platform inappropriately relied on contract as a legal basis to process personal data for service improvement purposes.
Instead, legitimate interest or consent seems a more appropriate legal basis in this case.
Indirect funding model
There are cases where a software company has an agreement with a third party to create or maintain an application to be able to share valuable data. In such cases, it is recommended to assess whether the third party is not a controller instead, and as such to be displayed in the privacy policy.
Consent or legitimate interest might be an available legal basis. For example, when the relation with such a third party is expected, legitimate interest could apply when a user directs the business to intentionally disclose personal information to a third party.
Conclusion
While it can seem easy to rely on data analytics as a generic purpose of processing, this does not reflect the GDPR's spirit or the purpose limitation principle, as confirmed by law enforcement and EDPB guidelines.
Data analytics must not always be seen as an umbrella for multiple personal data processing activities. Different legal bases can be available and applied for each purpose of processing.
Organizations should carefully assess their specific context and determine which legal basis would be most appropriate. The multiple possible uses of analytics data create a temptation to use such data points creatively. While some processing purposes allow for flexibility, they are not interchangeably substituted for the same purpose.
http://dlvr.it/T1sQvw
It is common to come across privacy notices indicating personal data is being processed for analytics purposes. In such cases, a single legal basis is often pointed out. But can data analytics be considered only one purpose for processing, grounded in a single legal basis under the GDPR?
Analytics: What are we talking about?
Analytical data is used to support systematic analysis, such as inspecting, transforming and modeling data to extract useful information, draw conclusions and patterns, and support decision-making.
Data analytics can be divided into two layers: the raw data layer, comprising user events and actions, and the metadata layer, processed and analyzed information derived from the raw data that is transformed into meaningful insights through techniques or tools.
The raw data layer represents the granular and detailed information collected during user interactions with applications and systems, while the analytics metadata layer represents the higher level insights and conclusions drawn from analyzing such raw data.
User actions refer to the various activities and behaviors individuals perform while interacting with an application, like user authentication, button clicking, typing, data inputting, scrolling, downloading, uploading, sharing and liking.
User events are specific occurrences that are tracked or logged during a user's interaction with a system or application and do not necessarily require affirmative actions. Events can be page or frame views, system errors, or transactional events.
As for the metadata layer, common events, in e-commerce apps for example, include the shopping cart abandonment rate, conversion rate and average order value — that is, the average amount spent by customers in a single transaction.
It is worth mentioning that some websites collect analytics through cookies, which then trigger application of the EU's ePrivacy Directive.
Purposes of processing for data analytics
Determining the processing purpose for data analytics should delve into the intent of the data collection and its intended use. This is because the same user data can be used for multiple analyses and, therefore, collected for different purposes. As so, not all purposes of data processing can be based on the same legal basis and may require different privacy by-design implementations to ensure lawfulness, such as:
* Monitoring application security and availability — like analyzing app crashes, debugging and troubleshooting, detecting anomalies, ensuring security traceability, and assuring app performance.
* Improving service, including by uncovering user patterns, trends, correlations and insights to improve existing and future features, as well as evaluating user engagement and creating user personas.
* Utilizing indirect funding models, where data is shared with third parties.
* Integrating business intelligence needs, such as supporting strategic decision-making and defining and monitoring key performance indicators.
* Utilizing service personalization, where the app itself contains an analytics board, or when specific user events and actions trigger specific app events, such as knowledge article recommendations.
This list is not exhaustive. Data analysts will likely find other interesting potential uses.
Anonymized processing of data analytics
Some organizations may have an option to process anonymized data for analytical purposes. Anonymized data is not identified or identifiable, and thus, it is not personal data and is out of the scope of privacy protection, as stated in GDPR Recital 26. The problems of defining a legal basis would not apply.
Application security, availability and service personalization
Monitoring application security, availability and service personalization may be considered parts of the service provision and, thus, able to rely on the performance of a contract — Article 6(1)(b) of the GDPR — as the legal basis for processing. It is generally in the user's interest to have means to keep data secure and protected when contracting a service, and logging is a common feature of most security frameworks. When the service value is intrinsically connected to in-app analytics or content personalization, such processing also counts as part of the service.
In such cases, consent is not an available legal basis because users generally could not freely withdraw consent while continuing to use the service. The European Data Protection Board's guidelines on consent state, "Generally, consent can only be an appropriate lawful basis if a data subject is offered control and is offered a genuine choice with regard to accepting or declining the terms offered or declining them without detriment."
Conversely, when the in-app analytics or personalized features are optional or not essential for the service provision, consent or legitimate interest may serve as a legal basis.
Service improvement
EDPB guidelines emphasize that Article 6(1)(b) would generally not be an appropriate lawful basis for processing personal data to improve service. In the EDPB's words, "while the possibility of improvements and modifications to a service may routinely be included in contractual terms, such processing usually cannot be regarded as being objectively necessary for the performance of the contract with the user."
This is also in the EDPB's binding decision on the dispute submitted by Ireland's Data Protection Commission regarding WhatsApp Ireland, in which the EDPB decided the platform inappropriately relied on contract as a legal basis to process personal data for service improvement purposes.
Instead, legitimate interest or consent seems a more appropriate legal basis in this case.
Indirect funding model
There are cases where a software company has an agreement with a third party to create or maintain an application to be able to share valuable data. In such cases, it is recommended to assess whether the third party is not a controller instead, and as such to be displayed in the privacy policy.
Consent or legitimate interest might be an available legal basis. For example, when the relation with such a third party is expected, legitimate interest could apply when a user directs the business to intentionally disclose personal information to a third party.
Conclusion
While it can seem easy to rely on data analytics as a generic purpose of processing, this does not reflect the GDPR's spirit or the purpose limitation principle, as confirmed by law enforcement and EDPB guidelines.
Data analytics must not always be seen as an umbrella for multiple personal data processing activities. Different legal bases can be available and applied for each purpose of processing.
Organizations should carefully assess their specific context and determine which legal basis would be most appropriate. The multiple possible uses of analytics data create a temptation to use such data points creatively. While some processing purposes allow for flexibility, they are not interchangeably substituted for the same purpose.
http://dlvr.it/T1sQvw
Ring Will No Longer Allow Police to Request Doorbell Camera Footage From Users
Amazon-owned Ring will stop allowing police to request doorbell camera footage from users following criticism from privacy advocates.
The post Ring Will No Longer Allow Police to Request Doorbell Camera Footage From Users appeared first on SecurityWeek.
http://dlvr.it/T1s3hm
The post Ring Will No Longer Allow Police to Request Doorbell Camera Footage From Users appeared first on SecurityWeek.
http://dlvr.it/T1s3hm
Hackers de plataformas cripto roubaram cerca de US$1,7 bi em 2023, diz relat?rio
(Reuters) - Hackers de plataformas de criptomoedas roubaram cerca de 1,7 bilh?o de d?lares em 2023, cerca de 54,3% menos que no ano anterior, mostrou relat?rio da Chainalysis nesta quarta-feira.
http://dlvr.it/T1rpm5
http://dlvr.it/T1rpm5
quarta-feira, 24 de janeiro de 2024
Tempestade solar poder? provocar desde instabilidade no r?dio a mudan?a da cor do c?u
A Terra poder? sofrer, nos pr?ximos dias, os impactos de m?ltiplas erup??es solares identificadas entre o ?ltimo domingo (21) e esta ter?a-feira (23) pelo Centro de Previs?o de Tempo Espacial, da Administra??o Nacional Oce?nica e Atmosf?rica (NOAA, na sigla em ingl?s), dos Estados Unidos.
http://dlvr.it/T1pv7m
http://dlvr.it/T1pv7m
Megavazamento de 26 bilhões de registros tem dados da Tencent, MySpace e LinkedIn
Da rede social profissional, pelo menos 231 milhões de registros foram vazados. A maior parte -1,5 bilhão - pertence à clientes da empresa de jogos e mídia social Tencent.
http://dlvr.it/T1pqsg
http://dlvr.it/T1pqsg
eBay cortar? 1.000 empregos e reduzir? contratos
(Reuters) - o eBay Inc cortar? cerca de 1.000 cargos, ou cerca de 9% de sua for?a de trabalho atual, informou a companhia de com?rcio eletr?nico na ter?a-feira.
http://dlvr.it/T1pV00
http://dlvr.it/T1pV00
'Haver? sinais': voc? est? caindo em um golpe e esses s?o os ind?cios
Os golpes virtuais se tornaram uma febre perigosa em nosso pa?s. Pelo menos 71% dos brasileiros j? sofreram alguma tentativa de fraude eletr?nica, mostra pesquisa publicada em junho de 2023 pela Nord Security, empresa de seguran?a digital.
http://dlvr.it/T1pHy2
http://dlvr.it/T1pHy2
terça-feira, 23 de janeiro de 2024
Governo vai capacitar 30 servidores em Privacidade e Segurança
Curso será presencial e terá 16 meses de duração. Entre os temas, gestão de incidentes cibernéticos.
http://dlvr.it/T1mkMT
http://dlvr.it/T1mkMT
Taming the beast: 7 tips for privacy professionals to facilitate responses to DSARs, reduce risk and build trust
Many privacy professionals rightly think data has become a "beast" within their company. Across the enterprise, business units, product managers and engineers have been given varying degrees of autonomy to develop their own internally and externally hosted applications, tools, data repositories, cloud stores and other systems.
They often have limited visibility of how their decisions to collect, copy, store and share data will impact the company's broader privacy compliance program. They also tend to focus on optimizing their systems to achieve business goals and may not prioritize paying attention to their systems' support of privacy compliance procedures.
At the same time, data privacy laws are proliferating. State privacy laws are adopted with increasing frequency, and federal and non-U.S. privacy requirements continue to expand. These privacy laws confer robust rights for individual data subjects and impose corresponding obligations on companies. Awareness of privacy rights is also increasing, and plaintiff's firms, class action lawsuits and regulatory enforcement actions are escalating privacy-related risks.
The old ways do not work very well
In the past, privacy pros could find ways to make privacy compliance work. Data subject access requests and other rights requests could be handled via manual procedures to query application owners and respond promptly. Governance of personal information, while not perfect, could also be managed. The old ways, however, do not seem to work well anymore.
Companies are experiencing a rapid increase in the frequency and complexity of DSARs, creating strains on manual response procedures. In the midst of cyber incidents, companies find sensitive personal information scattered within impacted, unstructured data repositories, obligating them to make data privacy breach notifications. Given the general proliferation of data, companies find it increasingly challenging to implement retention and secure deletion policies throughout their systems.
Privacy pros are making inroads, but going deeper is better
Privacy pros are working on many levels to make inroads. Workflow management tools are available to help track the intake, execution, and return of DSARs and other requests procedurally. Front-end cookie management tools can automate opt outs and consents from targeted marketing campaigns if properly configured. Data discovery tools can help to automate portions of the data discovery aspects of DSARs, and data deletion tools can help remove personal information from company systems.
Privacy pros could also benefit from working directly with company engineers and business teams to establish technical controls for the full lifecycle of personal information collection through deletion. This should involve collaborative efforts to develop and implement data classification, tagging, inventory, retention/deletion and overall data privacy governance. From a data privacy compliance perspective, this could help facilitate responses to DSARs, assure timely deletion of personal information when no longer required and overall data governance, and reduce the amount of personal information in unstructured data repositories to manage privacy risk in cyber incidents. From a business perspective, the benefits include better organized data that can be more easily utilized in a privacy-friendly manner that supports artificial intelligence, machine learning and other initiatives. Perhaps more fundamentally, this approach could help build customer trust by facilitating DSAR responses and mitigating privacy and cyber incident risks.
7 tips for aligning with engineers and business teams
How can privacy pros align more closely with company engineers and business teams?
1. Do the homework on how privacy law obligations apply at a systems level
From an engineering perspective, privacy laws impose various performance standards on company systems. It is helpful to think in these terms when preparing for discussions with engineers and business teams. Conceptually, privacy laws impose performance standards at three different points in the data lifecycle: during the collection of personal information, during the use and processing of personal information, and at the end of the data lifecycle.
Privacy pros need to "boil down" the privacy requirements in the expanding array of state, federal and non-U.S. privacy laws as they apply to the company's systems. This is not easy. Privacy laws are typically drafted based on the regulators' general notions of privacy principles and rights, which are not easily translated into concrete standards for implementation. Moreover, globally, regulators have broad authority to establish privacy requirements tailored to their philosophies, so companies need to deal with different and sometimes conflicting privacy law obligations.
For example, with respect to consent management issues, the EU ePrivacy Directive and the EU General Data Protection Regulation generally require prior express opt-in consent for advertising and other nonessential cookies.
In contrast, apart from sensitive personal information considerations, U.S. state privacy laws allow these cookies so long as implicit opt-out consent rights are provided and properly communicated to data subjects. Similarly, the Virginia Consumer Data Protection Act and the Colorado Privacy Act establish general express opt-in consent obligations for sensitive personal information collection and processing, as does the GDPR. In contrast, the Utah Consumer Privacy Act establishes an implicit opt-out requirement for any processing beyond providing the product or service for such data. The California Consumer Privacy Act requires the provision of opt-out consent to limit the use or disclosure of sensitive personal information.
Divergences also arise with respect to DSARs and data subject rights more broadly. For example, the Virginia, Colorado and Iowa privacy laws provide exemptions from DSARs and deletion rights for pseudonymized personal information under certain conditions, but comparable exemptions are not established under the CCPA or the GDPR. Various other exceptions and limitations apply with respect to data subject access, deletion, objection and other rights across privacy laws in different geographies and industry verticals.
Privacy pros will need to make decisions about consolidating these various privacy law obligations into performance standards that can be digestible by engineers and business teams. In some cases, privacy pros may suggest adopting a higher standard across the board to reduce friction and streamline implementation across jurisdictions. For example, although Utah's privacy law and the CCPA allow opt-out approaches concerning sensitive personal information, a privacy pro might recommend consideration of an express opt-in approach generally with ongoing opt-out rights to address Virginia and Colorado's privacy laws, the GDPR and other jurisdictions that establish higher express opt-in consent requirements.
Privacy pros might also consider the regulatory regimes too divergent to reconcile in some cases, so different implementations on the front end are needed. For example, the GDPR definitions and requirements on cookies are so different from U.S. state laws the company may wish to deploy one front end to users in the EU with its specific disclosures and requirements and a different approach for users in the U.S.
Importantly, privacy pros should approach business teams with recommendations and insights into privacy law requirements and participate in robust discussions to identify options and solutions, but generally should avoid making final decisions on privacy risk issues for the company. Privacy laws pose business and privacy risks, and senior business leaders are in the best position to make the final decisions on these issues. For more context on the privacy professional's role, see this article on applying privacy laws by understanding their meaning, assessing associated risks and accounting for other compliance obligations.
2. Make recommendations for handling data classification from a privacy law perspective
Each company is different, but for many a core issue will be specifying when or under what circumstances data collections about customers or other data subjects rise to the level of personal information, i.e., the definitional trigger for the application of many privacy laws.
Personal information is typically defined as any information about an identified or reasonably identifiable natural person, but different privacy laws can establish different definitions. Moreover, privacy laws can establish different standards for deidentifying/anonymizing personal information. And privacy laws can establish various thresholds for when personal information should be subject to a heightened degree of protection as "sensitive" personal information.
Companies in different industry verticals and business lines can diverge significantly as to whether or when they collect and process sensitive personal information. It is important bring informed recommendations regarding the scope of the company's processing activities concerning such sensitive personal information to discussions with engineering and business teams. For engineers, proper data classification will be foundational for the next steps of data tagging, inventory and overall data governance.
3. Align the business case
When making the business case internally to go deeper with engineers and business teams, think broadly about what other stakeholders would benefit from the exercise. Perhaps most directly, the compliance unit can benefit from better organized and scalable response procedures for DSARs, data subject requests and general broader data privacy compliance.
Cyber and information security can benefit due to reduced personal information found within unstructured data and other repositories and reduced risk of privacy breach notifications. Legal can benefit from having better organized information to search in the context of e-discovery and other investigations. Business teams can benefit with more organized datasets for AI, ML and other applications. Perhaps most importantly, the business will benefit from enhanced customer trust through more streamlined responses to DSARs and mitigated risks from privacy and cybersecurity issues.
4. Be strategic with whom to engage and look for opportunities
Without a forcing event to bring the issue to senior management's attention, many privacy pros would find it challenging to succeed in making a broad proposal for a large-scale investment in data privacy engineering. It would be better for privacy pros to be strategic about finding a business unit, product team or functional area more inclined to pursue improvements. It can also be helpful to look for opportunities to raise the idea with senior leadership, such as in a spin-off transaction, a data migration to the cloud, an IT transformation, or the "lessons learned" review after a significant cyber incident. Success on discrete, specific matters can establish the groundwork for large-scale initiatives that senior leadership will support and appreciate over time.
5. Focus on vendors and third-party disclosures
In terms of scope of effort, it is important to focus on the disclosure of personal information to vendors and third parties. This can be an area of significant privacy risk, and it will take a concerted effort to apply the privacy controls developed with engineering to such disclosures, both from a contractual perspective and from a technical perspective. This effort may involve the company's procurement teams, engineers and product managers.
6. Leverage information security governance.
Given the escalation of cyber risk over recent years, many companies have established well-developed information security governance teams and procedures to help manage cybersecurity risk. Privacy pros may find their company has good muscle memory with how to do security governance, and often, those procedures can be leveraged for better privacy implementation in a faster and more reliable manner.
7. Look for ways to bridge the gap
In many respects, the fundamental point of the exercise is bridging the gap between privacy pros who know the privacy laws and engineering, product and technical teams who design and implement the systems for the company. Privacy pros should work on both sides of that equation. Reading a privacy engineering book, taking an online class and/or asking an engineering colleague will give them a primer. At the same time, privacy pros should offer training to small or large groups on the aspects of privacy laws discussed above. The engineers and business teams can help guide them on where and how the privacy issues appear within the product development lifecycle. These teams can be tremendous allies in spotting and remediating privacy issues to which privacy pros would never have had visibility.
The road ahead
At the end of the day, this is a great time to be a privacy pro. Given the proliferation of privacy laws and risk, combined with the reality that data is critical for business, companies need skilled privacy pros more than ever. Over time, a privacy professional who knows the privacy laws and collaborates closely with engineering and business teams should be able to enhance privacy compliance, build customer trust and tame the beast of their company's data.
http://dlvr.it/T1mCvX
They often have limited visibility of how their decisions to collect, copy, store and share data will impact the company's broader privacy compliance program. They also tend to focus on optimizing their systems to achieve business goals and may not prioritize paying attention to their systems' support of privacy compliance procedures.
At the same time, data privacy laws are proliferating. State privacy laws are adopted with increasing frequency, and federal and non-U.S. privacy requirements continue to expand. These privacy laws confer robust rights for individual data subjects and impose corresponding obligations on companies. Awareness of privacy rights is also increasing, and plaintiff's firms, class action lawsuits and regulatory enforcement actions are escalating privacy-related risks.
The old ways do not work very well
In the past, privacy pros could find ways to make privacy compliance work. Data subject access requests and other rights requests could be handled via manual procedures to query application owners and respond promptly. Governance of personal information, while not perfect, could also be managed. The old ways, however, do not seem to work well anymore.
Companies are experiencing a rapid increase in the frequency and complexity of DSARs, creating strains on manual response procedures. In the midst of cyber incidents, companies find sensitive personal information scattered within impacted, unstructured data repositories, obligating them to make data privacy breach notifications. Given the general proliferation of data, companies find it increasingly challenging to implement retention and secure deletion policies throughout their systems.
Privacy pros are making inroads, but going deeper is better
Privacy pros are working on many levels to make inroads. Workflow management tools are available to help track the intake, execution, and return of DSARs and other requests procedurally. Front-end cookie management tools can automate opt outs and consents from targeted marketing campaigns if properly configured. Data discovery tools can help to automate portions of the data discovery aspects of DSARs, and data deletion tools can help remove personal information from company systems.
Privacy pros could also benefit from working directly with company engineers and business teams to establish technical controls for the full lifecycle of personal information collection through deletion. This should involve collaborative efforts to develop and implement data classification, tagging, inventory, retention/deletion and overall data privacy governance. From a data privacy compliance perspective, this could help facilitate responses to DSARs, assure timely deletion of personal information when no longer required and overall data governance, and reduce the amount of personal information in unstructured data repositories to manage privacy risk in cyber incidents. From a business perspective, the benefits include better organized data that can be more easily utilized in a privacy-friendly manner that supports artificial intelligence, machine learning and other initiatives. Perhaps more fundamentally, this approach could help build customer trust by facilitating DSAR responses and mitigating privacy and cyber incident risks.
7 tips for aligning with engineers and business teams
How can privacy pros align more closely with company engineers and business teams?
1. Do the homework on how privacy law obligations apply at a systems level
From an engineering perspective, privacy laws impose various performance standards on company systems. It is helpful to think in these terms when preparing for discussions with engineers and business teams. Conceptually, privacy laws impose performance standards at three different points in the data lifecycle: during the collection of personal information, during the use and processing of personal information, and at the end of the data lifecycle.
Privacy pros need to "boil down" the privacy requirements in the expanding array of state, federal and non-U.S. privacy laws as they apply to the company's systems. This is not easy. Privacy laws are typically drafted based on the regulators' general notions of privacy principles and rights, which are not easily translated into concrete standards for implementation. Moreover, globally, regulators have broad authority to establish privacy requirements tailored to their philosophies, so companies need to deal with different and sometimes conflicting privacy law obligations.
For example, with respect to consent management issues, the EU ePrivacy Directive and the EU General Data Protection Regulation generally require prior express opt-in consent for advertising and other nonessential cookies.
In contrast, apart from sensitive personal information considerations, U.S. state privacy laws allow these cookies so long as implicit opt-out consent rights are provided and properly communicated to data subjects. Similarly, the Virginia Consumer Data Protection Act and the Colorado Privacy Act establish general express opt-in consent obligations for sensitive personal information collection and processing, as does the GDPR. In contrast, the Utah Consumer Privacy Act establishes an implicit opt-out requirement for any processing beyond providing the product or service for such data. The California Consumer Privacy Act requires the provision of opt-out consent to limit the use or disclosure of sensitive personal information.
Divergences also arise with respect to DSARs and data subject rights more broadly. For example, the Virginia, Colorado and Iowa privacy laws provide exemptions from DSARs and deletion rights for pseudonymized personal information under certain conditions, but comparable exemptions are not established under the CCPA or the GDPR. Various other exceptions and limitations apply with respect to data subject access, deletion, objection and other rights across privacy laws in different geographies and industry verticals.
Privacy pros will need to make decisions about consolidating these various privacy law obligations into performance standards that can be digestible by engineers and business teams. In some cases, privacy pros may suggest adopting a higher standard across the board to reduce friction and streamline implementation across jurisdictions. For example, although Utah's privacy law and the CCPA allow opt-out approaches concerning sensitive personal information, a privacy pro might recommend consideration of an express opt-in approach generally with ongoing opt-out rights to address Virginia and Colorado's privacy laws, the GDPR and other jurisdictions that establish higher express opt-in consent requirements.
Privacy pros might also consider the regulatory regimes too divergent to reconcile in some cases, so different implementations on the front end are needed. For example, the GDPR definitions and requirements on cookies are so different from U.S. state laws the company may wish to deploy one front end to users in the EU with its specific disclosures and requirements and a different approach for users in the U.S.
Importantly, privacy pros should approach business teams with recommendations and insights into privacy law requirements and participate in robust discussions to identify options and solutions, but generally should avoid making final decisions on privacy risk issues for the company. Privacy laws pose business and privacy risks, and senior business leaders are in the best position to make the final decisions on these issues. For more context on the privacy professional's role, see this article on applying privacy laws by understanding their meaning, assessing associated risks and accounting for other compliance obligations.
2. Make recommendations for handling data classification from a privacy law perspective
Each company is different, but for many a core issue will be specifying when or under what circumstances data collections about customers or other data subjects rise to the level of personal information, i.e., the definitional trigger for the application of many privacy laws.
Personal information is typically defined as any information about an identified or reasonably identifiable natural person, but different privacy laws can establish different definitions. Moreover, privacy laws can establish different standards for deidentifying/anonymizing personal information. And privacy laws can establish various thresholds for when personal information should be subject to a heightened degree of protection as "sensitive" personal information.
Companies in different industry verticals and business lines can diverge significantly as to whether or when they collect and process sensitive personal information. It is important bring informed recommendations regarding the scope of the company's processing activities concerning such sensitive personal information to discussions with engineering and business teams. For engineers, proper data classification will be foundational for the next steps of data tagging, inventory and overall data governance.
3. Align the business case
When making the business case internally to go deeper with engineers and business teams, think broadly about what other stakeholders would benefit from the exercise. Perhaps most directly, the compliance unit can benefit from better organized and scalable response procedures for DSARs, data subject requests and general broader data privacy compliance.
Cyber and information security can benefit due to reduced personal information found within unstructured data and other repositories and reduced risk of privacy breach notifications. Legal can benefit from having better organized information to search in the context of e-discovery and other investigations. Business teams can benefit with more organized datasets for AI, ML and other applications. Perhaps most importantly, the business will benefit from enhanced customer trust through more streamlined responses to DSARs and mitigated risks from privacy and cybersecurity issues.
4. Be strategic with whom to engage and look for opportunities
Without a forcing event to bring the issue to senior management's attention, many privacy pros would find it challenging to succeed in making a broad proposal for a large-scale investment in data privacy engineering. It would be better for privacy pros to be strategic about finding a business unit, product team or functional area more inclined to pursue improvements. It can also be helpful to look for opportunities to raise the idea with senior leadership, such as in a spin-off transaction, a data migration to the cloud, an IT transformation, or the "lessons learned" review after a significant cyber incident. Success on discrete, specific matters can establish the groundwork for large-scale initiatives that senior leadership will support and appreciate over time.
5. Focus on vendors and third-party disclosures
In terms of scope of effort, it is important to focus on the disclosure of personal information to vendors and third parties. This can be an area of significant privacy risk, and it will take a concerted effort to apply the privacy controls developed with engineering to such disclosures, both from a contractual perspective and from a technical perspective. This effort may involve the company's procurement teams, engineers and product managers.
6. Leverage information security governance.
Given the escalation of cyber risk over recent years, many companies have established well-developed information security governance teams and procedures to help manage cybersecurity risk. Privacy pros may find their company has good muscle memory with how to do security governance, and often, those procedures can be leveraged for better privacy implementation in a faster and more reliable manner.
7. Look for ways to bridge the gap
In many respects, the fundamental point of the exercise is bridging the gap between privacy pros who know the privacy laws and engineering, product and technical teams who design and implement the systems for the company. Privacy pros should work on both sides of that equation. Reading a privacy engineering book, taking an online class and/or asking an engineering colleague will give them a primer. At the same time, privacy pros should offer training to small or large groups on the aspects of privacy laws discussed above. The engineers and business teams can help guide them on where and how the privacy issues appear within the product development lifecycle. These teams can be tremendous allies in spotting and remediating privacy issues to which privacy pros would never have had visibility.
The road ahead
At the end of the day, this is a great time to be a privacy pro. Given the proliferation of privacy laws and risk, combined with the reality that data is critical for business, companies need skilled privacy pros more than ever. Over time, a privacy professional who knows the privacy laws and collaborates closely with engineering and business teams should be able to enhance privacy compliance, build customer trust and tame the beast of their company's data.
http://dlvr.it/T1mCvX
Logitech tem resultado acima do esperado no trimestre
(Reuters) - O novo presidente-executivo da Logitech International disse nesta ter?a-feira que a empresa trabalhar? para voltar a crescer, uma vez que prev? que as vendas anuais diminuir?o menos do que o previsto anteriormente e afirmou que o faturamento da companhia no trimestre passado superou as expectativas.
http://dlvr.it/T1m0k1
http://dlvr.it/T1m0k1
Pre?o do Samsung Galaxy S23 FE caiu mais de R$ 1.000; ? hora de comprar?
No final de 2023, n?s falamos aqui no Guia de Compras UOL sobre o Samsung Galaxy S23 FE (Fan Edition), lan?ado em outubro do ano passado para ser o modelo "baratinho" da linha S23. S? que na ?poca ele estava mais caro que o Galaxy S23, mesmo com uma configura??o inferior, e o nosso veredito foi que a compra n?o compensava.
http://dlvr.it/T1lk44
http://dlvr.it/T1lk44
segunda-feira, 22 de janeiro de 2024
Parcelado sem juros: Senacon revoga medida cautelar contra empresas de pagamento
PagSeguro, Mercado Pago, Stone e PicPay prestaram esclarecimentos à pasta e a Secretaria, ligada ao Ministério da Justiça, sustentou que as instituições demonstraram o cumprimento das normativas legais. "A SENACON impediu mais um avanço contra o parcelado sem juros", afirmou a presidente da Abranet, Carol Conway.
http://dlvr.it/T1kBJf
http://dlvr.it/T1kBJf
Chinese Spies Exploited VMware vCenter Server Vulnerability Since 2021
CVE-2023-34048, a vCenter Server vulnerability patched in October 2023, had been exploited as zero-day for a year and a half.
The post Chinese Spies Exploited VMware vCenter Server Vulnerability Since 2021 appeared first on SecurityWeek.
http://dlvr.it/T1jQ8B
The post Chinese Spies Exploited VMware vCenter Server Vulnerability Since 2021 appeared first on SecurityWeek.
http://dlvr.it/T1jQ8B
France Fines Yahoo 10 Mn Euros Over Cookie Abuses
France's data protection watchdog fines Yahoo 10 million euros for not respecting users' refusals of internet-tracking "cookies"
The post France Fines Yahoo 10 Mn Euros Over Cookie Abuses appeared first on SecurityWeek.
http://dlvr.it/T1jPwZ
The post France Fines Yahoo 10 Mn Euros Over Cookie Abuses appeared first on SecurityWeek.
http://dlvr.it/T1jPwZ
EDPB Publishes One-Stop-Shop Digest on Data Security and Breach Notification
On January 18, 2024, the European Data Protection Board published a thematic one-stop-shop case digest titled, “Security of Processing and Data Breach Notification.” Continue Reading
http://dlvr.it/T1jLlN
http://dlvr.it/T1jLlN
Jap?o celebra informa??es da sonda lunar e acredita em seu restabelecimento
O Jap?o desligou sua sonda lunar quase tr?s horas ap?s seu hist?rico pouso na Lua no s?bado (20), para permitir a recupera??o da nave, informou a ag?ncia espacial nesta segunda-feira (22).?
http://dlvr.it/T1jCGk
http://dlvr.it/T1jCGk
domingo, 21 de janeiro de 2024
FTC Reminds AI Companies to Uphold Privacy Commitments
On January 9, 2024, the Federal Trade Commission published a blog post reminding artificial intelligence (“AI”) “model-as-a-service” companies to uphold the privacy commitments they make to customers, including promises made in Terms of Service agreements, promotional materials and online marketplaces. “Model-as-a-service” companies develop AI products and make them available to customers via end-user interfaces... Continue Reading
http://dlvr.it/T1gwzt
http://dlvr.it/T1gwzt
sábado, 20 de janeiro de 2024
Nasa perde contato com seu helic?ptero em Marte
A Nasa perdeu contato com seu pequeno helic?ptero "Ingenuity" em Marte, que fazia seu 72? voo, anunciou a ag?ncia espacial americana, acrescentando que tentava restabelecer a comunica??o.
http://dlvr.it/T1fDVf
http://dlvr.it/T1fDVf
Sonda japonesa pode ficar sem energia ap?s pousar na Lua
O Jap?o se tornou, neste s?bado (20), o quinto pa?s do mundo a conseguir fazer um pouso bem sucedido na Lua, mas sua sonda, SLIM, est? ficando sem energia devido a um problema em seu sistema de baterias solares.
http://dlvr.it/T1f325
http://dlvr.it/T1f325
Desoneração da folha: no embate Pacheco x Haddad, Lula quer ser a palavra final
Presidente da República fez duras críticas à desoneração da folha, mas quer se reunir com o presidente do Senado, Rodrigo Pacheco para tratar do tema. Ministro da Fazenda chegou a dizer que 'as desonerações não renderam um emprego ou um aumento de salário para ningúem".
Rodrigo Pacheco enfrenta Haddad e Lula e diz que desoneração da folha vale até 2027
http://dlvr.it/T1dgFL
Rodrigo Pacheco enfrenta Haddad e Lula e diz que desoneração da folha vale até 2027
http://dlvr.it/T1dgFL
sexta-feira, 19 de janeiro de 2024
SP, Rio e Bahia lideram pedidos de bloqueios no Celular Seguro
Programa completa primeiro mês de operação com uma média de 393,4 pedidos de bloqueio por dia.
http://dlvr.it/T1c6c3
http://dlvr.it/T1c6c3
Hermano Tercius assume secretaria de Telecomunicações do MCom
Ex-anatel, Hermano Tercius assume a função até então exercida por Maximiliano Martinhão.
http://dlvr.it/T1c3f8
http://dlvr.it/T1c3f8
Rodrigo Pacheco enfrenta Haddad e diz que desoneração da folha vale até 2027
Fora do Brasil, o presidente do Senado, Rodrigo Pacheco (PDD/MG), descartou qualquer acordo com o governo sobre a reoneração da folha, como quer o ministério da Fazenda. Segundo ele, há o compromisso do governo de reeditar uma nova Medida Provisória para derrubar o texto da MP 1202.
http://dlvr.it/T1bmbP
http://dlvr.it/T1bmbP
Jap?o tenta chegar ? Lua com seu m?dulo Moon Sniper
O m?dulo Moon Sniper do Jap?o iniciar? na meia-noite de sexta-feira para s?bado (20) a sua tentativa de chegar ? Lua, que, se for bem-sucedida, colocaria o arquip?lago asi?tico no seleto grupo de pa?ses a conseguir um pouso controlado no sat?lite da Terra.
http://dlvr.it/T1bhjK
http://dlvr.it/T1bhjK
Reddit pretende lan?ar IPO em mar?o, dizem fontes
(Reuters) - A plataforma de m?dia social Reddit tem tra?ado planos detalhados para lan?ar uma oferta p?blica inicial (IPO) em mar?o, avan?ando com uma listagem que est? no radar h? mais de tr?s anos, de acordo com fontes familiarizadas com o assunto.
http://dlvr.it/T1bPLh
http://dlvr.it/T1bPLh
quinta-feira, 18 de janeiro de 2024
Ransomware Group Targets Foxconn Subsidiary Foxsemicon
Foxsemicon’s website defaced with a message from the LockBit ransomware group, which claims to have stolen 5 Tb of data.
The post Ransomware Group Targets Foxconn Subsidiary Foxsemicon appeared first on SecurityWeek.
http://dlvr.it/T1Yb72
The post Ransomware Group Targets Foxconn Subsidiary Foxsemicon appeared first on SecurityWeek.
http://dlvr.it/T1Yb72
Curso de Inteligência Artificial gratuito tem 1000 vagas disponíveis em todo o país
Iniciativa, batizada de QualiFacti, é da Facti, Instituição Científica e Tecnológica (ICT), e faz parte do programa MCTI Futuro. Inscrições vão até o dia 29 de fevereiro.
http://dlvr.it/T1YZfk
http://dlvr.it/T1YZfk
Governo Digital: Brasscom quer CNPJ como meio de autenticação no Gov.br
Contribuição da entidade de TIC à Estratégia Nacional de Governo Digital também sugere o uso dos ATMs dos bancos públicos como canal de atendimento. Brasscom sugere ainda o fim da obrigatoriedade de manter os dados armazenados em data centers locais.
http://dlvr.it/T1YHS9
http://dlvr.it/T1YHS9
The importance of mental health in cyber security
Mental health in cybеr security industry is a critical but often overlooked aspect of the wellbeing of professionals in this field
http://dlvr.it/T1Xvm5
http://dlvr.it/T1Xvm5
quarta-feira, 17 de janeiro de 2024
Dez mil firewalls SonicWall estão expostos a ataques de DDoS
Pesquisadores de segurança descobriram que mais de 178 mil firewalls de próxima geração (NGFW) da SonicWall estão com a interface de gerenciamento exposta online e vulneráveis a ataques de negação de serviço (DoS) e possíveis ataques de execução remota de código (RCE).
http://dlvr.it/T1W2LY
http://dlvr.it/T1W2LY
Legislação e enquadramento sindical de trabalhadores em teletrabalho
Regulamentado pelo Artigo 75-B da Consolidação das Leis do Trabalho (CLT), o teletrabalho presenta peculiaridades que visam equilibrar a flexibilidade inerente a essa modalidade com a necessidade de proteger os direitos dos trabalhadores.
http://dlvr.it/T1W1zS
http://dlvr.it/T1W1zS
Anatel faz nova tomada de subsídios para discutir seu papel na regulação das big techs
Contribuições vão até o dia 15 de abril. Vale lembrar que a LGT trata os prestadores de SVA (classificação que inclui plataformas digitais) como usuários.
http://dlvr.it/T1Vkp5
http://dlvr.it/T1Vkp5
YouTube ganha dinheiro com nova cruzada de negacionismo clim?tico, diz grupo de monitoramento
(Reuters) - O YouTube est? ganhando milh?es de d?lares por ano com publicidade em canais que fazem afirma??es falsas sobre mudan?a clim?tica porque os criadores de conte?do est?o usando novas t?ticas que driblam as pol?ticas da plataforma de m?dia social para combater a desinforma??o, de acordo com um relat?rio publicado nesta ter?a-feira.
http://dlvr.it/T1VLnJ
http://dlvr.it/T1VLnJ
terça-feira, 16 de janeiro de 2024
FBot: cuidado esse malware quer roubar a sua nuvem
Ferramenta é baseada na linguagem Python e está sendo usada pelos hackers para sequestrar plataformas em nuvme e serviços de pagamento.
http://dlvr.it/T1SCl0
http://dlvr.it/T1SCl0
Governo e Congresso negociam sobrevida à desoneração da folha
O líder do governo no Senado, Jaques Wagner (PT/BA) descartou a devolução da MP 1202 ainda durante o recesso parlamentar pelo Congresso Nacional. Mas sinalizou que não se pode ter 'perdedores e vencedores' , o que significa uma flexibilidade em relação à medida.
http://dlvr.it/T1S9sd
http://dlvr.it/T1S9sd
Contra 'gatonet', TV paga inclui Netflix e Globoplay em pacotes no Brasil
Como estrat?gia de combater o 'gatonet' e a consequ?ncia queda de contrata??es que atingem o Brasil nos ?ltimos anos, as TVs por assinatura visam as plataformas de streamings como aliadas para reten??o de clientes e diminuir a sangria vivida no mercado.
http://dlvr.it/T1S7mN
http://dlvr.it/T1S7mN
Vers?o russa da Wikip?dia ser? lan?ada nesta segunda-feira, diz m?dia
(Reuters) - O lan?amento em grande escala do Ruwiki, uma vers?o russa da popular enciclop?dia da internet Wikip?dia, ocorrer? nesta segunda-feira, de acordo com a m?dia russa.
http://dlvr.it/T1RrW1
http://dlvr.it/T1RrW1
segunda-feira, 15 de janeiro de 2024
GitLab Patches Critical Password Reset Vulnerability
GitLab has resolved a critical authentication vulnerability allowing attackers to hijack password reset emails.
The post GitLab Patches Critical Password Reset Vulnerability appeared first on SecurityWeek.
http://dlvr.it/T1PlJm
The post GitLab Patches Critical Password Reset Vulnerability appeared first on SecurityWeek.
http://dlvr.it/T1PlJm
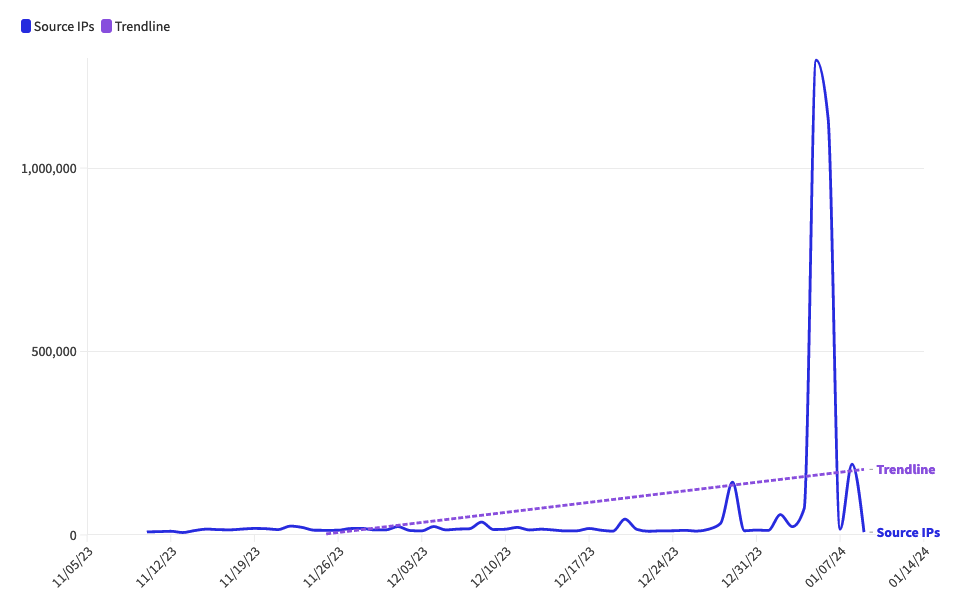
Cloud Server Abuse Leads to Huge Spike in Botnet Scanning
Netscout sees over one million IPs conducting reconnaissance scanning on the web due to increase in use of cheap or free cloud servers.
The post Cloud Server Abuse Leads to Huge Spike in Botnet Scanning appeared first on SecurityWeek.
http://dlvr.it/T1Pl5Q
The post Cloud Server Abuse Leads to Huge Spike in Botnet Scanning appeared first on SecurityWeek.
http://dlvr.it/T1Pl5Q
Juniper Networks Patches Critical Remote Code Execution Flaw in Firewalls, Switches
Juniper Networks patches over 100 vulnerabilities, including a critical flaw that can be exploited for remote code execution against firewalls and switches.
The post Juniper Networks Patches Critical Remote Code Execution Flaw in Firewalls, Switches appeared first on SecurityWeek.
http://dlvr.it/T1PkrY
The post Juniper Networks Patches Critical Remote Code Execution Flaw in Firewalls, Switches appeared first on SecurityWeek.
http://dlvr.it/T1PkrY
Prazer para todos: estes sex toys funcionam em sincronia e at? como bateria
Muitas das inova??es exibidas na CES (Consumer Eletronic Show), uma das maiores feiras de tecnologia do mundo, envolvem TVs inusitadas, prot?tipos de carros el?tricos deslizando em palcos enormes e rob?s para facilitar uma s?rie de coisas. Agora, uma categoria de dispositivos que fez sucesso na edi??o deste ano n?o tem nada a ver com isso: os sex toys.
http://dlvr.it/T1PQlX
http://dlvr.it/T1PQlX
Assinar:
Postagens (Atom)
Teles vão ao STF contra adicional de ICMS no Rio de Janeiro e Alagoas
ADIs questionam aumento do tributo para custeio de fundos de combate à pobreza. http://dlvr.it/T6DWkm